

Sphere Security, a trusted leader in cybersecurity solutions. Under the guidance of our Managing Director, Shubham Kumbhar, we are committed to safeguarding businesses with our comprehensive range of services. As part of the esteemed Kumbhar Group of Companies, we uphold the highest standards of excellence.
Our services include Secure SDLC, DevSecOps implementation, and Security Consultant on hire, ensuring holistic protection throughout the software development lifecycle. Additionally, we offer VAPT, Security Awareness Training, Security Consulting, and Advisory services, along with expert Threat Modeling.

Zero Trust Consulting and Advisory service empowers organizations to analyze all possible security threats from a neutral perspective. It encompasses not limited to but all security landscapes, including
Securing software code at earlier development stages can save cost by more than 5 times in comparison to introducing security at later stages
Secure SDLC ensures that applications are compliant and secure as per global standards. You can hire our consultants on a monthly retainer to help you secure your applications and assist your software team with better cyber security implementations and recurring VAPT audits.


Updates within technology are required every time which may lead to configuration drift
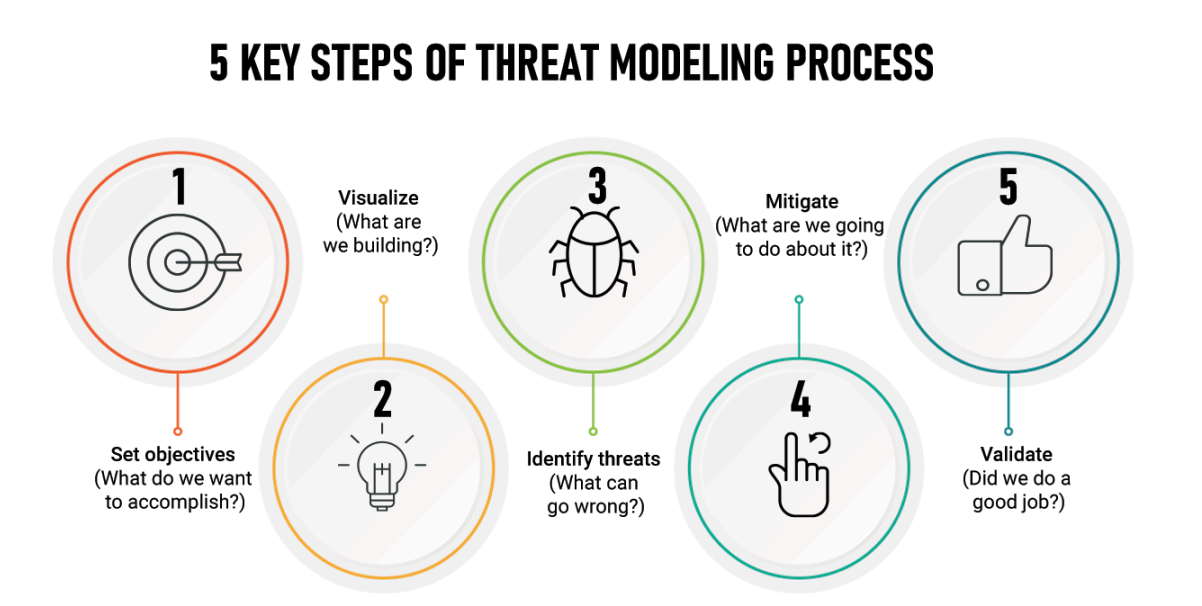
Threat Modelling document includes detailed bugs and threats from the past helping to evolve security posture with every update and avoiding recursive work
Automation brings a leisure to most activities which are repetitive. Monitoring security on every update is a similar struggle which is usually in need of automation.
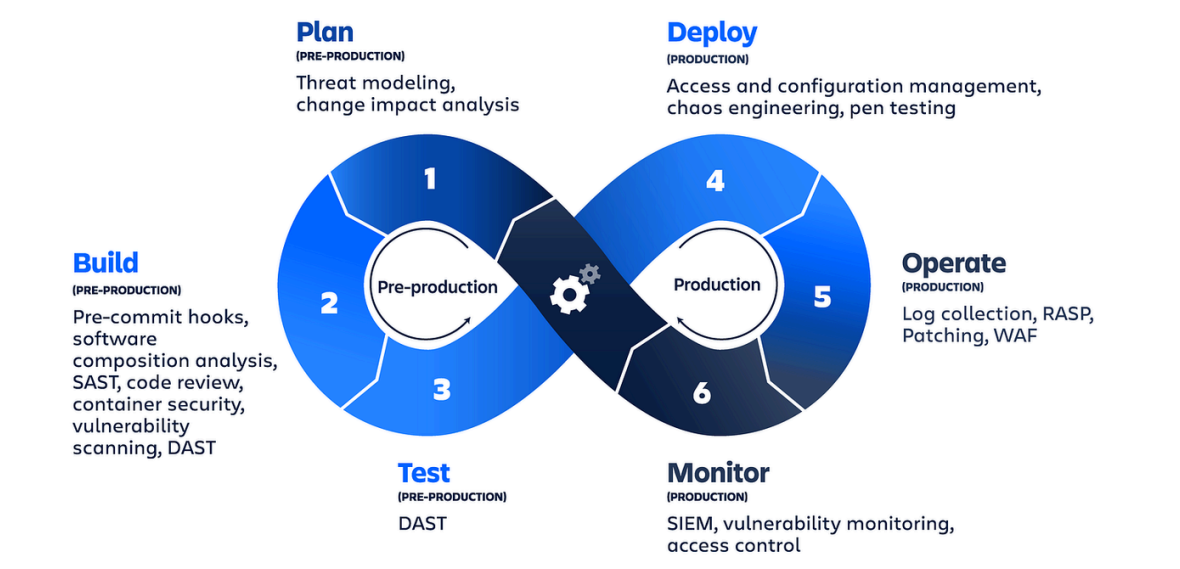
DevSecOps brings you the expertise to automate your security efforts and get reports on every security issue before code moves to production

Enhance your software development with our expert Security Consultant services. We prioritize proactive security to fortify your software solutions against cyber threats from inception to deployment.
With our comprehensive suite of security consulting services, we empower your development teams to build secure, reliable, and resilient software solutions that meet the highest standards of security and compliance.
By the end of the training, participants will emerge with the knowledge and confidence to navigate the digital landscape safely, protect themselves and their organizations from cyber threats, and contribute to building a secure cyberculture.



Our VAPT (Vulnerability Assessment and Penetration Testing) services rigorously assess your systems for weaknesses. Through thorough examination and simulated attacks, we identify vulnerabilities and provide actionable insights to fortify your defenses. Safeguard your digital assets with our comprehensive VAPT solutions.